Leveraging the Power of the Well-Architected Framework
Barry Turner
Senior Consultant, ISSI
During a recent audit I asked the partner, "How useful is the Well-Architected Framework." The response surprised me. "We started using it to pass the audits, and now it's fundamental to many of our processes."
This blog will provide an overview of the Well-Architected Framework (WAF), the benefits it delivers, and how to start using it. I will also briefly discuss the role of the WAF in conjunction with the Cloud Adoption Framework.
What is the Well-Architected Framework?
The Well-Architected Framework made its first appearance when AWS launched a program around about eight years ago. The WAF outlined the principles of cloud architectural design best practices across these five cloud-computing "pillars":
- Security: Maximize the security of your data and workloads in the cloud, design for privacy, and align with regulatory requirements and standards.
- Cost optimization: Optimize usage and rate utilization while keeping a cost-efficient mindset.
- Operational excellence: Streamline operations with standards, comprehensive monitoring, and safe deployment practices.
- Performance optimization: Design and tune your cloud resources for optimal performance.
- Reliability: Ensure the ability of a workload to perform its intended function correctly and consistently when it's expected to.
The WAF simplified the articulation of cloud architectural best practices into easy-to-digest statements. I'll refer to these as the "standard pillars" throughout this blog.
Today cloud vendors have embraced the WAF, albeit with different names or structures. Alibaba Cloud, AWS, and Microsoft have all published individual versions of the Well-Architected Framework. Google Cloud has its "Google Cloud Architecture Framework" and refers to "categories" rather than "pillars." These four vendors have a similar structure based on the five standard pillars. Oracle has its Best Practices Framework for Oracle Cloud Infrastructure; this is a whitepaper that covers the standard pillars. The link for the white paper is shown below in the reference section.
IBM and VMware take a different approach. IBM uses the five standard pillars and adds a sixth, Portable and Hybrid. VMware approaches the subject from a different perspective by providing a framework for multi-cloud scenarios, using five pillars called Plan, Build, Secure, Modernize, and Operate.
In addition to the five standard pillars, AWS recently added sustainability:
- The Sustainability pillar focuses on environmental impacts, especially energy consumption and efficiency, since they are important levers for architects to inform direct action to reduce resource usage.
The IBM has a Hybrid and Portable pillar is described as:
- Hybrid is the ability to run workloads in and across one or more public clouds, private clouds, and on-premises.
Regardless of the vendor, each pillar or category defines a set of best practice design guidelines. For example, in security it entails the use of least-privilege access / Role Based Access Control and enforced multi-factor authentication. Operational Excellence examples include using DevOps for deployment, and automating standard tasks such as patching.
There are three standard ways to use the Well-Architected Framework:
- Design workload architectures that comply with the best practices.
- Deploy infrastructure using templates and blueprints that are aligned with the best practices.
- Review existing workloads against the Well-Architected Framework to identify gaps, and then remediate the gaps when applicable.
Why use the Well-Architected Framework?
Cloud services are highly dynamic and customer requirements are constantly evolving, so the best-practice architecture for a workload is likely to evolve over time. The Well-Architected Framework provides a methodology to ensure that solution designs are aligned with the vendor's best practices regardless of this constant change.
The WAF benefits these groups:
- Cloud End Users: The cloud end user experiences optimized costs, reduced security risks, improved performance, and reduced operational and reliability risks. All of which enhance customer satisfaction.
- The Channel Partner: Many partners generate revenue and margin by providing consulting services based on the WAF. This typically includes providing a "Well-Architected Review" as a service, design documentation based on the five pillars, and service management reporting based on the five pillars. Demonstrating to customers that the solution design is aligned with the vendor's best practices is a great way to build customer confidence. Additionally, workloads aligned with the framework typically reduce operational and support costs, improving partner profitability.
- The Cloud Vendor: Optimizing costs, minimizing the risks associated with cloud migration, and optimizing workload performance drives increased customer satisfaction and spending. In addition, ensuring that partners' and customers' workloads are aligned with the design best practices reduces the vendor's operational and support costs.
How does the Well-Architected Framework fit with the Cloud Adoption Framework?
In discussing the WAF we also need to talk about the Cloud Adoption Framework (CAF), Which is which is a framework adopted by several of the vendors to describe a strategic approach to cloud adoption. CAF gives companies migrating to the cloud a set of strategic phases that increase the likelihood of the project achieving its business objectives. While each of the vendors has its version of CAF, for this blog I will summarize these as strategy, plan, environment readiness, adoption, governance, and management. CAF generally applies at the strategic level across the cloud environment and all migrated workloads. The Well-Architected Framework complements this and is applied at the workload level.
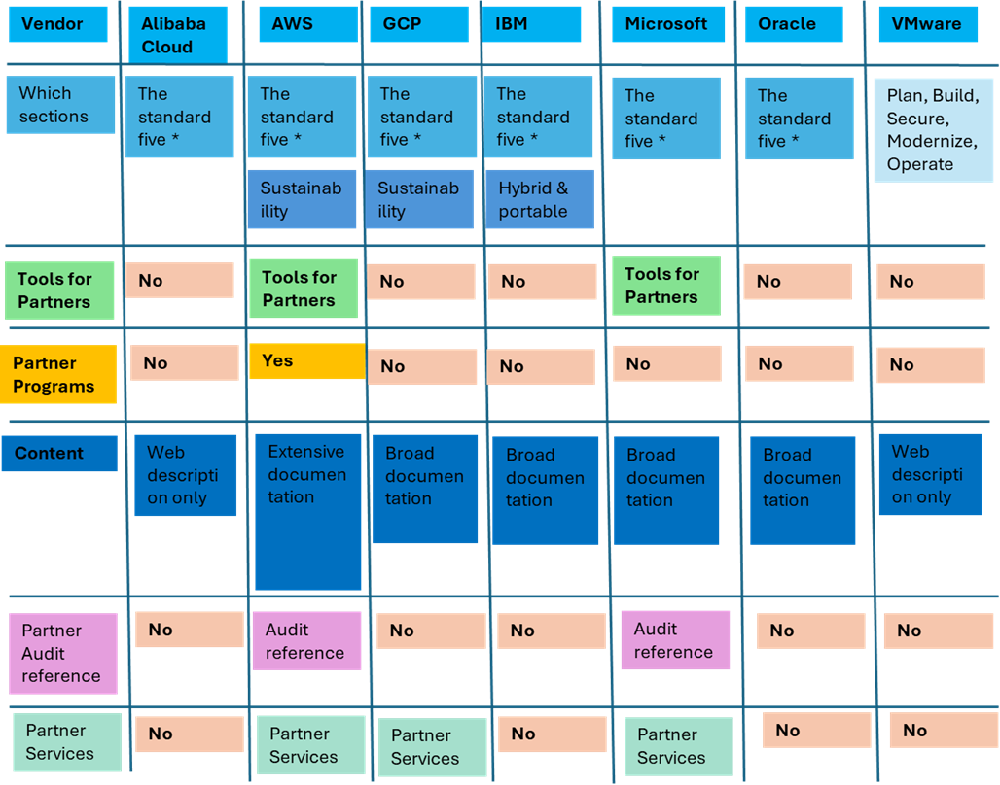
Vendor approach
The table below shows the different approaches taken by the cloud vendors. They all provide documentation to varying degrees of detail. In addition, AWS and Microsoft provide a set of well-architected tools and use the framework in the partner audit processes. AWS takes this one step further with the AWS Well-Architected Partner Program, which ensures that participating partners have a high level of expertise and experience in implementing the Well-Architected Framework.
Next steps
Cloud Partners: Develop services based on a Well-Architected Framework. Examples include:
- Structuring solution design documentation around the five or six pillars.
- Providing a well-architected workload review service.
- Cloud-managed service providers embed the five or six pillars in the standard service reporting and include an annual well-architected review in the top tier of services.
- If your organization has not yet adopted the Well-Architected Framework, encourage the engineering team to include it in the annual development plan and use the tools the vendors provide.
Cloud End Users: When migrating IT services to the cloud, companies and individuals should:
- Work with their chosen cloud partner or reseller to implement the Well-Architected Framework.
- When selecting a new cloud supplier use implementation of the Well-Architected Framework as a procurement requirement.
- Encourage cloud technical teams to become trained in the Well-Architected Framework.
The author: Barry Turner is a Senior Consultant at ISSI and has worked with a broad range of cloud partners and vendors since 2015. He has 27 years of service creation experience working with telecommunication and cloud service providers across EMEA on behalf of ISSI, Microsoft, Cisco, Mitel & Agile Programmes. He currently holds ITIL V4 Foundation, Customer Success Manager Level 2, ISO27001:2013 lead auditor certifications and is PMP certified.
As a leading consulting firm partnering closely with top cloud technology companies, ISSI is uniquely positioned to guide you through your cloud partner transformation journey. Let us help you unlock the full potential of this opportunity. Contact us today to begin your transformation. For more information, contact us at: sales@issi-inc.com
References
AWS
https://aws.amazon.com/architecture/well-architected/
Google
https://cloud.google.com/architecture/framework
Microsoft
https://learn.microsoft.com/en-us/azure/well-architected/
Oracle
https://docs.oracle.com/en/solutions/oci-best-practices/toc.htm
https://www.oracle.com/uk/cloud/oci-best-practices-guide/
IBM
https://www.ibm.com/architectures/well-architected
Alibaba
https://www.alibabacloud.com/help/en/well-architected
VMware
https://vmc.techzone.vmware.com/resource/whitepaper-vmware-cloud-well-architected-framework#audience
General
https://www.lucidchart.com/blog/aws-well-architected-framework-best-practices
https://versent.com.au/blog/how-you-can-benefit-from-the-aws-well-architected-framework/
https://azure.microsoft.com/en-gb/solutions/cloud-enablement/well-architected#reliability
https://www.cloud-bridge.co.uk/blog/best-practice-with-an-aws-well-architected-review
CAF vs WAF
https://www.cloud4c.com/blogs/cloud-adoption-framework-versus-well-architected-framework
https://techcommunity.microsoft.com/t5/azure-architecture-blog/why-you-need-a-cloud-adoption-framework-caf-and-probably-a-waf/ba-p/3667426
Additional Articles
The Value of Service Processes for Cloud Managed Service Providers (MSPs)
Barry Turner, Senior Consultant, ISSIISSI works with partners across a spectrum of business models who want to become cloud-managed service providers. Within that ecosystem are two types of partners who can face a stumbling block on the way to becoming MSPs: cloud native partners and resellers.
Project Plan Vs. Success Plan Vs. Adoption Plan
Jonathan Lee, ISSI Customer Success Practice LeadProject Plan Vs. Success Plan Vs. Adoption Plan There are differences and this is when to apply them By Jonathan Lee – ISSI Customer Success
How to implement customer success in managed services
Jonathan Lee, ISSI Customer Success Practice LeadHow to Implement Customer Success in Managed Services By Jonathan Lee – ISSI Customer Success Practice Lead Customer Success Practice Blog Series #5 In my
- 10 SEP 2024
Microsoft's AI Cloud Partner Program: A New Way to Empower Partners
Pablo Marrone, ISSI Senior ConsultantThese start with the most basic - Membership - which is open to all channel partners. From there they progress through partner success; the attainment of “designations” based on partner capability scores; and finally, “specializations” that
13 MAR 2024Demystifying audits: a guide for partners
ISSI Regional Lead TeamDemystifying Audits: A Guide for Partners By ISSI Regional Lead Team The word "audit" can often strike fear in the hearts of business owners. But...
24 JUL 2023Building a solid strategy for becoming a cloud managed service provider
Barry Turner, ISSI Head of Global Marketing & Senior ConsultantCloud Management Platforms: A Core Component in Growing Your Managed Services Business By Amarnath Gutta, Senior Consultant, ISSI In our work with partners through workshops,
